Windows PowerShell Remoting: Host Based Investigation and Containment Techniques
In this blog post I will detail how to perform various incident response techniques using native Windows PowerShell functionality. Each method I explain will be able to be executed remotely to allow for efficient investigation and containment of an individual host. For PowerShell response on mass, I recommend familiarising yourself with the Kansa framework.
If you follow my github, you may also notice that many of the techniques listed below are built into my remote powershell triage tool, B2Response, which allows you to perform these actions with ease. Please give it a go and provide feedback!
The techniques which I will cover include:
1) Issuing remote command/shell
2) Retrieving/downloading files
3) Checking for running processes
4) Query registry keys
5) PCAP collection
6) Blocking a domain
7) Blocking an IP
8) Quarantining a host
To establish the initial session on the remote host, use the following command (replacing 'remotehost' with the remote host computer name):
We can now refer to the $s1 variable for subsequent commands and they will be executed through this session.
PowerShell Prompt
To access the PowerShell session and enter manual commands on the remote host, enter the following command.
Individual PowerShell Command
To execute a single PowerShell command (or command block) on a remote host, enter the following command.
PowerShell Script Execution
To execute a PowerShell script on a remote host, enter the following command.
In this command we are copying the file "C:\Users\bob\Downloads\maliciousdoc.docx' on the remote host to our local D:\triagefiles folder.
A limitation to this method is that you will not able able to download files which are protected (such as registry hives). In order to download these files, you will need to use a third party tool such as RawCopy, which can be remotely executed with ease using B2Response.
This is useful if you know which key you need to look in, however there are many other registry keys malware may use to persist on a system. As a good starting point, I would recommend running autorunsc to check multiple locations. B2Response can execute this tool remotely using PowerShell with ease.
So let's open C:\Windows\System32\drivers\etc\hosts in your favourite text editor (I will use Notepad++) as Administrator and append the following line:
Save the file.
Note: The `n adds a new line to the file.
Once this script is executed on a host, it will perform the same modification that we manually made to the hosts file. To block multiple domains, simply add additional Add-Content commands to the blockdomains.ps1.
To execute this script on our remote PC, use the script execution command we learnt earlier:
To unblock this IP address, run the following command:
Apply Quarantine:
Once applied, this computer will not be able to initiate any outbound connections to either internal or external (including internet) resources. Don't be surprised if you don't receive feedback from this command, or further commands, as the PC cannot send traffic outbound anymore!
If you would like to roll back this quarantine action, you can simply issue this command to the same device to remove the quarantine firewall rule. This should work, as the host can still receive inbound connections and process the command.
Remove Quarantine:
If you follow my github, you may also notice that many of the techniques listed below are built into my remote powershell triage tool, B2Response, which allows you to perform these actions with ease. Please give it a go and provide feedback!
The techniques which I will cover include:
1) Issuing remote command/shell
2) Retrieving/downloading files
3) Checking for running processes
4) Query registry keys
5) PCAP collection
6) Blocking a domain
7) Blocking an IP
8) Quarantining a host
Prerequisites
All of the techniques listed below utilise PowerShell to remotely manage computers within your IT environment. In order for these techniques to work, you must have your environment configured to permit PowerShell remoting and you must be running the commands from a user who has privileges to execute remote PowerShell commands. For more information on how to set this up, please read this article.
Let's get started!
Initial Setup - Establish a Remote Session!
Throughout this blog post, I will be describing how to execute various PowerShell remoting commands. Whilst it is possible to issue these commands individually, I prefer to establish a PowerShell session first, and then refer to this session in subsequent commands.
The reason I prefer to establish a session first is that I use the -NoMachineProfile session option, which restricts creation of a user profile on the remote host. By establishing this session once and then referring to that session for each subsequent command, it reduces the chance that I will forget to include this session option and expose myself on the target machine.
The reason I prefer to establish a session first is that I use the -NoMachineProfile session option, which restricts creation of a user profile on the remote host. By establishing this session once and then referring to that session for each subsequent command, it reduces the chance that I will forget to include this session option and expose myself on the target machine.
What would I need to prevent profile creation on the remote host?
Preventing creating of your user profile on the remote host will save you lots of potential headache when investigating alerts in a corporate environment. Imagine that you have to investigate your senior executes for suspicious activity. If that senior executive then sees your user profile on his PC, he may think you were snooping on his computer. Save yourself the hassle and setup your session with stealth!
To establish the initial session on the remote host, use the following command (replacing 'remotehost' with the remote host computer name):
$s1 = New-PSsession -ComputerName remotehost -SessionOption (New-PSSessionOption -NoMachineProfile) -ErrorAction Stop
We can now refer to the $s1 variable for subsequent commands and they will be executed through this session.
1) Issuing Remote Commands & Remote Shell
When researching security products, I found it quite surprising that very few products supported remote command execution on the host. When I asked vendors about it, most vendors stated that it was coming very soon on their feature road map, as it was a highly requested feature.
Remote command execution can be very useful for enumerating the current state of the host, and can be achieved very easily with PowerShell. Many commands throughout this blog post are simply applications of the following remote command execution techniques.
Remote command execution can be very useful for enumerating the current state of the host, and can be achieved very easily with PowerShell. Many commands throughout this blog post are simply applications of the following remote command execution techniques.
PowerShell Prompt
To access the PowerShell session and enter manual commands on the remote host, enter the following command.
Enter-PSSession -Session $s1
Individual PowerShell Command
To execute a single PowerShell command (or command block) on a remote host, enter the following command.
Invoke-Command -ScriptBlock {Get-Process} -Session $s1
PowerShell Script Execution
To execute a PowerShell script on a remote host, enter the following command.
Invoke-Command -file file.ps1 -Session $s1
2) Downloading Files
Sometimes we may want to download a file from a remote host to our local machine in order to perform further analysis. To download a file, execute the following command:
Copy-Item -Path "C:\Users\bob\Downloads\maliciousdoc.docx" -Destination "D:\triage_files" -FromSession $s1I
In this command we are copying the file "C:\Users\bob\Downloads\maliciousdoc.docx' on the remote host to our local D:\triagefiles folder.
A limitation to this method is that you will not able able to download files which are protected (such as registry hives). In order to download these files, you will need to use a third party tool such as RawCopy, which can be remotely executed with ease using B2Response.
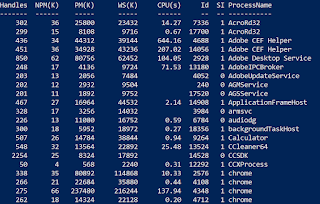
3) Check Running Processes
To check running processes, we can remotely execute Get-Process using the following command.
Invoke-Command -ScriptBlock { Get-Process} -Session $s1
4) Query Registry Keys
Querying registry keys can be a useful way to identify the presence of malware on a system. One common registry key I will use as an example is the HKLM\Software\Microsoft\Windows\CurrentVersion\Run key.What is HKLM\Software\Microsoft\Windows\CurrentVersion\Run ?
This registry key contains a list of programs and their arguments which get executed every time Windows boots. As a result, many malware will add an entry to this registry key so that the malware runs on each boot.To view the contents of this registry key on our remote host, use the following command
Invoke-Command -ScriptBlock {Get-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run} -Session $s1
This is useful if you know which key you need to look in, however there are many other registry keys malware may use to persist on a system. As a good starting point, I would recommend running autorunsc to check multiple locations. B2Response can execute this tool remotely using PowerShell with ease.
5) Packet Capture
Thanks to some fantastic work by nospaceships, it is incredibly easy to capture network traffic into a wireshark compatible PCAP file with PowerShell. This capture method works by using raw sockets to capture IP packets on a specified network interface.
What are raw sockets?
A TCP/IP raw sockets is a type of socket which provides access to the underlying transport provider. In this scenario, it provides access to the specific network interface which allows us to capture the network traffic to a .pcap file.
Implementation of this packet capture method requires two stages.
Stage 1) Identify the network interface to capture on
Executing the following command will list the available network interfaces.
In this example, we will be capturing on the wireless interface, which was listed in the output of the ipconfig command.
We need to note down the IPv4 address for stage 2, which in this case is 192.168.1.100.
Stage 2) Run the pcap script
The following script will download nospaceships raw-socket-sniffer script, execute it and save the pcap to 'capture.pcap' in the current working directory of the remote host.
Ensure that you replace the -InterfaceIP parameter with the IP address identified in stage 1, or your pcap may be empty.
Because we ran the session with the -NoMachineProfile option, the raw-socket-sniffer.ps1 and capture.cap should be located under C:\Windows\System32.
You can now use the 'Download file' instructions from this blog post to download the capture.pcap to your local system for analysis in WireShark.
Stage 1) Identify the network interface to capture on
Executing the following command will list the available network interfaces.
Invoke-Command -ScriptBlock {ipconfig} -Session $s1
In this example, we will be capturing on the wireless interface, which was listed in the output of the ipconfig command.
We need to note down the IPv4 address for stage 2, which in this case is 192.168.1.100.
Stage 2) Run the pcap script
The following script will download nospaceships raw-socket-sniffer script, execute it and save the pcap to 'capture.pcap' in the current working directory of the remote host.
Ensure that you replace the -InterfaceIP parameter with the IP address identified in stage 1, or your pcap may be empty.
Invoke-Command -ScriptBlock { $url = "https://raw.githubusercontent.com/nospaceships/raw-socket-sniffer/master/raw-socket-sniffer.ps1" Invoke-WebRequest -Uri $url ` -OutFile "raw-socket-sniffer.ps1" PowerShell.exe -ExecutionPolicy bypass .\raw-socket-sniffer.ps1 ` -InterfaceIp "192.168.1.100" ` -CaptureFile "capture.cap" } -Session $s1
Because we ran the session with the -NoMachineProfile option, the raw-socket-sniffer.ps1 and capture.cap should be located under C:\Windows\System32.
You can now use the 'Download file' instructions from this blog post to download the capture.pcap to your local system for analysis in WireShark.
6) Blocking a Domain
In this example we will be redirecting malicious traffic destined for http://bad.com/ to the localhost, which effectively blocks network connections to this domain. To do this we will edit the Windows hosts file.
What is the Windows hosts file?
The Windows hosts file is located at C:\Windows\System32\drivers\etc\hosts on Win 7+ and Server 2003+ systems and contains mappings of IP addresses to host names. We can use this to redirect traffic destined for a specific domain to a specific IP address. The file has no extension, but is a normal text file that can be edited with notepad.
What is localhost?
Localhost is a networking term which refers to the current computer. In this scenario, we will be redirecting malicious traffic to localhost, where it will fail to be received, as there is no service listening for the traffic (unless you are running a web server).
Shouldn't we be blocking/sinkholing on the network layer?
Absolutely. Automated domain sinkholing at a network layer is a fantastic control. There are however many scenarios where network sinkholing may not reach all devices in your environment. I've seen many environments where remote devices aren't configured for full tunnel back to on premise firewalls, so the host goes straight out to the internet (bypassing a firewall sinkhole).
127.0.0.1 bad.com
Save the file.
Now when we visit bad.com in a browser we cannot reach this location, because traffic is being redirected to the localhost, which isn't hosting a web server.
Lets automate this with PowerShell. Copy the following code into Notepad++ and save it as blockdomains.ps1
Add-Content C:\Windows\System32\drivers\etc\hosts "`n127.0.0.1 bad.com"
Note: The `n adds a new line to the file.
Once this script is executed on a host, it will perform the same modification that we manually made to the hosts file. To block multiple domains, simply add additional Add-Content commands to the blockdomains.ps1.
To execute this script on our remote PC, use the script execution command we learnt earlier:
Invoke-Command -file blockdomains.ps1 -Session $s1
7) Blocking an IP
The reasons unknown to me, the Windows firewall is often overlooked as an effective host based firewall.
What is a host based firewall?
A host based firewall is a software firewall that runs on an individual computer which defines what inbound and outbound network connections are allowed to/from that computer.
If you have identified connections to a malicious IP on a host, you can use the Windows firewall to block connections to this IP.
In order to block connections to a specific IP address (173.182.192.43 in this example) on a remote host, use the following command:
In order to block connections to a specific IP address (173.182.192.43 in this example) on a remote host, use the following command:
Invoke-Command -ScriptBlock {New-NetFirewallRule -DisplayName "Block_Malicious_IP" -Direction Outbound –LocalPort Any -Protocol TCP -Action Block -RemoteAddress 173.182.192.43} -Session $s1
To unblock this IP address, run the following command:
Invoke-Command -ScriptBlock {Remove-NetFirewallRule -DisplayName "Block_Malicious_IP"} -Session $s1
8) Quarantining a Host
Expanding on the Windows firewall's ability to block individual network connections, we can also apply firewall rules to block all outbound network connections, effectively quarantining the infected PC.What does it mean to quarantine a PC, and why would we do it?
Quarantining a PC is the act of segregating the device at a network level, as to limit the capability for the compromised of that device to spread to, or access, other computing resources within the IT environment.We can use the following PowerShell command to create a new Windows firewall rule called 'InfoSec_Quarantine' on a remote PC which we would like to quarantine.
Apply Quarantine:
Invoke-Command -ScriptBlock {New-NetFirewallRule -DisplayName InfoSec_Quarantine -Direction Outbound -Enabled True -LocalPort Any -RemoteAddress Any -Action Block} -Session $s1
Once applied, this computer will not be able to initiate any outbound connections to either internal or external (including internet) resources. Don't be surprised if you don't receive feedback from this command, or further commands, as the PC cannot send traffic outbound anymore!
If you would like to roll back this quarantine action, you can simply issue this command to the same device to remove the quarantine firewall rule. This should work, as the host can still receive inbound connections and process the command.
Remove Quarantine:
Invoke-Command -ScriptBlock {Remove-NetFirewallRule -DisplayName InfoSec_Quarantine} -Session $s1
Conclusion
I hope this post has helped some of you get started with PowerShell incident response techniques. If you have additional tasks you would like to perform with PowerShell, give them a go, and feel free to email me at b2dfir@gmail.com if you would like some help, or if you would like me to cover other topics in a future blog post.







This information was very helpful. Thanks for sharing. Firewall Errors Tech Support Number
ReplyDelete+1-800-293-9401
ReplyDeleteThanks for sharing this information with us and it was a nice blog.
DevOps Training
DevOps Online Training
ReplyDeleteThis is an awesome post.Really very informative and creative contents DevOps Training in Bangalore | Certification | Online Training Course institute | DevOps Training in Hyderabad | Certification | Online Training Course institute | DevOps Training in Coimbatore | Certification | Online Training Course institute | DevOps Online Training | Certification | Devops Training Online
I just want to thank you for sharing your information and your site or blog this is simple but nice Information I’ve ever seen i like it i learn something today. PowerShell
ReplyDeleteNice Blog !
ReplyDeleteAre you confronting annoying technical defects in QuickBooks while working on it? If yes, here is the solution!! Just reach out to our Customer Service Number For QuickBooks 1-888-927-O94O, and acquire favourable support.
Load runner online training
ReplyDeleteMSBI online training
Mule ESB online training
Mulesoft online training
Great Post, thanks for sharing such an amazing blog with us. Visit Ogen Infosystem for creative website design and PPC Services in Delhi, India.
ReplyDeleteWebsite Designing Company in India
ReplyDeleteHi
I visited your blog you have shared amazing information, i really like the information provided by you, You have done a great work. I hope you will share some more information regarding full movies online. I appreciate your work.
Thanks
Powershell Classes
Nice blog..
ReplyDeleteSAP mm training
SAP pm training
SAP PP training
SAP Qm training
SAP Sd training
SAP Security training
SAP Grc training from india
Windows Server Training
Thanks for sharing this amazing blog
ReplyDeleteBis Consultant in delhi
Thank you for your articles that you have shared with us. Hopefully you can give the article a good benefit to us. Microsoft Business Central Administración, Configuración y Gestión
ReplyDeleteThanks for Such a nice article, Please keep sharing article like this.
ReplyDeleteWebocity is best website designing company in delhi , Best Website development company in Delhi, We Offer Best Digital Marketing services in Delhi.
Do you need help with issues you are facing in QuickBooks? If so!! Then connect with our experts at Quickbooks Customer Service Phone Number USA | Canada +1-855-929-0120. and eliminate the obstacles to your workflow. They are available 24/7 with value for money services!!
ReplyDeleteQuickBooks Support Phone Number +1-855-929-0120
Quickbooks Customer Service Phone Number | Quickbooks Support +1-855-929-0120
Very nice blog, Thanks for sharing great article.
ReplyDeleteYou are providing wonderful information, it is very useful to us.
Keep posting like this informative articles.
Thank you.
Get to know about yts.
Thanks for writing case study-based content such wonderful informative content.
ReplyDeleteAlways ensure that the b2b data provided by data providers should follow a certain standard and high quality required to enhance your business ROI. You can choose the best method to make sure that this quality by researching the origin from where you
are fetching the information. It must be a reputable and trustworthy source.
Mua vé tại Aivivu, tham khảo
ReplyDeletevé máy bay đi Mỹ bao nhiêu
có thể bay từ mỹ về việt nam không
vé máy bay giá rẻ từ Canada về Việt Nam
các chuyến bay từ nhật về việt nam
Lịch bay từ Hàn Quốc về Việt Nam hôm nay
Vé máy bay từ Đài Loan về Việt Nam
Astonishing post! Thank you for creating such a wonderful collection of content
ReplyDeleteGo to www.office.com/setup for Office Setup. Sign In to your Microsoft Office Account.Find your Office Product Key.Enter your Microsoft Office Product Key.
Officecom is a way where you can save you file in OneDrive and you can share and update online.
webroot.com/safe is best Installation Guide.The security package offered by this brand is incredibly easy
to setup and install.
Our group is able and qualified to help with resolving your errors. Call us at QuickBooks Support Phone Number and get the best solution you need. Our one of expert will help your call and give you the right support you need. Call us at our QuickBooks Support Phone Number - QuickBooks Customer Number USA +1-888-897-4360 today and get the best solution.
ReplyDeleteWhile DIY detox methods will not provide drastic results, there are several professionally designed marijuana detox remedies and kits available online. Many detox kits also require drinking a lot of water to help dilute urine, but that is paired alongside several curated herbal supplements and nutrients, like creatinine, to mask intended dilution. When providing urine samples, the drug testing administrator will check for diluted urine. Insufficient nutrients in pee could indicate marijuana use and an attempt to hydrate to help pass the test. Instructions to use this kit are quite simple. Unbox the content of the ‘Quickest’ kit.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThanks. for sharing.
ReplyDeleteOffice furniture Dubai a private work desk attributes a delicately inlaid parquetry of premium. The leading contains a collection of office furniture in Dubai
It's really good Blog.Thanks for sharing!
ReplyDeleteDevOps Training
DevOps Online Training
In case you see errors in your QB, you can pass on our expert QuickBooks experts at QuickBooks Support Phone Number +1-541-876-5068. They can give you the right service.
ReplyDeleteNeed second QB support? Lets interface with us at Quickbooks Support Number + 1-855-857-3081 today. We can help with resolving your errors and give you the best solution. Along these lines, if you are confronting any sort of QB issues, you can call us at QuickBooks Technical Support Phone Number today and fix your issues immediately.
ReplyDeleteMake the essential strides not to spare one moment to call us at Quickbooks Phone Number +1-888-693-6862 if you are seeing issues and errors in your QuickBooks. We can help you with resolving your issues immediately. Taking care of QuickBooks errors can be a mind-boggling task. You might stand up to this issue while utilizing your QuickBooks.
ReplyDeleteIf you want to find out the ways to install the Netgear WNR2200 Firmware update, you must download the firmware and then save it. First of all, you should download the firmware and save it accordingly. You can unzip it if required. Now, log into the router with the help of a web browser and then click on the advanced tab administration firmware upgrade. Now, click on the browse and then find the file you just downloaded and then click on upload, and you must not interrupt.
ReplyDeleteWhen searching for right QB support, you have to talk with the technical support team of skilled individuals. Call us at our toll free Quickbooks Customer Service Phone Number and get your issues fixed.
ReplyDeleteOur team of expert QuickBooks Desktop Support Phone Number specialists have the ability and experience to fix the errors and issues that you are confronting. Call us at our QuickBooks Customer Service Phone Number today.
ReplyDeleteUpdate your work space with this Canon PIXMA across the board remote printer. Underlying connect canon pixma printer to wifi network makes getting to and creating archives from your cell phone or tablet basic. Inherent Wi-Fi network makes getting to and creating reports from your cell phone or tablet straightforward.
ReplyDeleteThis comment has been removed by the author.
ReplyDeletethanks for sharing nice blog https://snowflakemasters.in/
ReplyDeleteResetting a device brings it back to the original configuration and settings. Sometimes you forget the modifications you made in the router and are unable to login. In this case reset Epson printer to factory settings. Let’s take a look at the steps to complete the process.
ReplyDeletealanya eskort
ReplyDeleteafyon eskort
amasya eskort
bayburt eskort
yozgat eskort
ataköy eskort
düzce masöz
manisa masöz
Thanks for sharing this with so much of detailed information, its much more to learn from your article. Keep sharing such good stuff.Digital Marketing Guest postWith technological advancement, we have made our lives more comfortable and easier. However, since technology is advancing fast, not everyone can pace up with its speed.
ReplyDeleteHey friend, it is very well written article, thank you for the valuable and useful information you provide in this post. Keep up the good work! FYI, Pet Care adda
ReplyDeleteCredit card processing, wimpy kid books free
,Essay About Trip With Family
AnFXO Gateway can be used to connect several POTS lines; the gateways are typically available in 1, 2, 4, and 8-port versions. also Check Synway SMG1000-D Series FXS/FXO Gateway new Product for your business....
ReplyDeleteSalam UAE provides custom manufactured office furniture in Dubai, as well as wholesale distributors of office Executive Desk, Executive chairs, and luxury office furniture in Dubai, UAE. Office Furniture Dubai , Office Furniture in Dubai and Office Furniture Dubai
ReplyDeleteThis is one of the best posts I’ve read. It contains some very valuable and helpful information. Thanks for sharing. Smallville Crows Varsity Jacket
ReplyDeleteThis is great collection of shotguns at British shooting show. Punisher Jacket
ReplyDeletenice post..Cloud Service Provider In Wimbledon
ReplyDeleteCloud Solutions In London
cloud solutions in Wimbledon
Nice post. Thank you to provide us this useful information. Jamie Top Boy Puffer Jacket
ReplyDeleteAny creature can look at the WiFi Password Hacker Online section in the diagram and would like to use it for free. Hack Wifi Password Online Android
ReplyDeleteGet intelligent suggestions in the Editor Overview pane in Word and let Editor assist you across documents, email, and on the web MS Office 2016 Crack Key
ReplyDeleteDeep Dark Love Quotes quotations area unit simply phrases or quotes concerning deep love with such a splash of romance, tranquilly, and joy thrown certain smart live. Deep Dark Quotes
ReplyDeletemmorpg oyunlar
ReplyDeleteinstagram takipçi satın al
tiktok jeton hilesi
TİKTOK JETON HİLESİ
Saç ekim antalya
referans kimliği nedir
instagram takipçi satın al
metin2 pvp serverlar
instagram takipci satin al
This comment has been removed by the author.
ReplyDeleteIn the list of printers, Epson surely has acquired an exclusive position in the list because of its amazing service and great printing quality. Epson Printers play a vital role in enhancing features and great updates. But the users often witness issues and so they put up questions like how to troubleshoot an Epson WorkForce 500 Printer or why is my Epson WorkForce not printing? You can follow the steps and try to fix it without any fuss. Have a look at the steps.
ReplyDeleteHey,
ReplyDeleteThanks for sharing such nice information.
Are you from Canada, Ontario, and searching for the best Roofing Company Brampton? Here, We are in this business for the last couple of years and we know client satisfaction is a must. Our team members are highly experienced and dedicated to their work. best roofers in brampton
skylight installers near me
commercial roofing services near me
1인출장샵 1인출장샵 1인출장샵
ReplyDelete아산출장마싸지 천안출장마싸지 예산출장마싸지
Nice Blog, Thanks for Sharing. BE Global is offering SEO Service in Dubai at best price.
ReplyDeleteTo troubleshoot the issue of Avast VPN not working then you need to start by changing the VPN location. The solution to change the location of Avast VPN then follow the steps. For this, start by opening Avast VPN application and choose privacy option from left side of the screen. After that, click to change location button and choose another location that wasn’t selected before. Lastly, make the desired changes and exit. Your final step is to restart the computer and see whether the Avast VPN is resolved or not. https://prompthelp.us/blog/avast-vpn-not-working-problems/
ReplyDeletesmm panel
ReplyDeleteSmm Panel
iş ilanları
İnstagram Takipçi Satın Al
hirdavatciburada.com
beyazesyateknikservisi.com.tr
servis
jeton hile indir
Hi,
ReplyDeleteIt is really a great post by you. I found this so interesting. Keep it up and keep sharing such posts.
Making task is one of the pieces of a professional education that gives a superior comprehension of the subject to the understudy. The greater part of the understudies stuck while making their task. Are you additionally one of them. In the event that indeed, there are numerous task creators in market who will give assistance you in making your tasks and assist you with achieving passing marks.
A wide range of subjects where understudies generally look for online task help are BSBWOR203 assessment answers Help, Management Assignment Help, bsbdiv501 appraisal replies, and so on.
importance of a balanced diet
Great site article its too good.its great and easy to understand
ReplyDeleteMicrosoft Office Crack
UTorrent Pro Crack
Marvelous Designer Crack Mac
A interesting site blog this is superb.Its too good.
ReplyDeleteVideopad Video Editor Crack
Wondershare Filmora Crack
Honeycam Crack
Emeditor Crack
Serato DJ Crack
i love this one blog
ReplyDeletepetart
I am very impressed with your post because this post is very beneficial for me and provides knowledge to me.
ReplyDeleteRenee iPhone Recovery Crack
Corel AfterShot Pro Crack
Driver Talent Pro Crack
Tipard Video Converter Ultimate Crack
iSkysoft Video Converter Ultimate Crack
Just go through the steps and so you will be able to troubleshoot the issues associated with Brother HL L8260. Now, once you do follow the steps and so you will be able to resolve the issues without any fuss. Check out the steps to know more. Once you do follow and apply the steps, you will be able to troubleshoot your problems without any fuss.
ReplyDeleteNice blog, thanks for sharing
ReplyDeleteAPKSbio
Meetme MOd apk
This comment has been removed by the author.
ReplyDeletewow what is this really? Why aren't you doing this now? I think it's so awesome and awesome I have to share this with my friends and my son and wife right now I feel like I found an oasis in the desert Thank you so much for finding your site.평택출장아로마
ReplyDelete화성출장아로마
의정부출장아로마
동해출장아로마
삼척출장아로마
All of the techniques listed below utilise PowerShell to remotely manage computers within your IT environment. In order for these techniques to work, you must have your environment configured to permit PowerShell remoting and you must be running the commands from a user who has privileges to execute remote PowerShell commands.
ReplyDeleteSyncabackpro Crack blender crack
zmodeler crack
ReplyDeleteI really appreciate your valuable efforts and it was very helpful for me. Thank you so much...!
ReplyDeleteBest Divorce Lawyers in Arlington VA
ReplyDeleteYour website is awesome. I used a lot of what it had to say.
getting over it ocean of games
Thanks for sharing. BEglobalza is one of the leading Digital Marketing company in cape town .Our team of passionate experts ensures clear, hard-working, , honest and tangible results online.
ReplyDeleteAn unprecedented time is elapsed while overcoming your blog. Regardless, erverthing moves towards progress. For movement click here Office Furniture Dubai
ReplyDeleteI have gone through your blog content. It was really fabulous. But it still have gaps to get improved. For improvements Click here UAE Office Furniture
ReplyDeleteThanks for sharing. Hiking is fantastic in New Mexico, and there are lots of beautiful places to go. Here you can learn more about Hiking Destinations In New Mexico, USA.
ReplyDeleteVery Interesting Blog ! If You have any question Regrading Quickbooks Software during Installation and pupation then call a my toll free
ReplyDeleteQuickBooks Customer Support Phone Number: +1 855-729-7482 to resolve any problems
Great Blog Thank For Sharing With Us. If you need technical service for QuickBooks problems, dial Quickbooks Customer Support Phone Number +1 855-977-3297 for live chat support
ReplyDeleteQuickbooks is best software company which provide instant solution by expert at
ReplyDeleteQuickbooks Customer Support Number+12134170111
Thanks for sharing this useful Content. If you are Quickbooks User If you need technical service for QuickBooks problems, dial
ReplyDeleteQuickbooks Customer Support +1 855-729-7482
Great Blog content, Thanks For Sharing with us IF you are using QuickBooks accounting software for your business and feel something need then To get support for the software,
ReplyDeleteQuickbooks Customer Support Phone Number+1 267-773-4333
Good blog. If you are looking for QuickBooks help you can contact us at. Quickbooks Customer Support Number +1 855-428-7237
ReplyDeleteThanks for sharing this informative post. If you need help with your Quickbooks account, you can call
ReplyDeleteNice Information You can also click here to find Quickbooks issue contact Quickbooks Customer Service +1 855-377-7767
Thanks for this fantastic Blog!! Please check out about any Quickbooks query at
ReplyDeletequickbooks customer service+1 347-982-0046
Nice Content If your business is having any issues with Quickbooks software Then View more at quickbooks customer service+18559773297
ReplyDeleteGood blog, if you are looking for a Quickbooks Customer Service you can contact us at. +185542872371092 Atlanta, GA 30307, United States
ReplyDeleteNice post
ReplyDeletebankruptcy lawer near me
dc computer crime laws
very Good Information!!Are you searching for a genuine Quickbooks Information help you can take help for Quickbooks issue call at
ReplyDeleteQuickbooks Customer Support +1 877-755-5046
This comment has been removed by the author.
ReplyDeleteAre you facing issues Quickbooks Issue then you can contact
ReplyDeleteQuickbooks Customer Support +1 267-773-4333
Im really impressed your article.
ReplyDeletenew jersey divorce faq
Im really liked your article.
ReplyDeletedivorcio sin oposición virginia en línea
Thanks for sharing. Beglobalus is leading Web Development Company in Los Angeles. We specialize in helping businesses build eCommerce and lead generation focused websites.
ReplyDeleteNice blog article, thanks for sharing
ReplyDeletereact js training in hyderabad
Nice blog ever
ReplyDeleteJava Course in Hyderabad
Very good Informations ! If you are looking Regarding Quickbooks Issue you can get instant help in the at Quickbooks Customer Service +18663062642
ReplyDeleteI m very happy After Read Your Blog !! If you are looking Professional
ReplyDeleteQuickbooks Customer Service+18554442233 to get best technical solutions for QuickBooks errors.
I have read this blog completely I have got lot off information in it like "Whether you're looking for desks, chairs, cabinets, or other office furniture, you're sure to find a great selection in the UAE."
ReplyDeleteClick for more information office furniture in dubai
Office Furniture - Office furniture Dubai, UAE
https://multiwood.ae
This is an excellent article
ReplyDeleteselenium online training in hyderabad selenium online training in kphb>
If you want to know more about this software then you can contact Quickbooks Customer Support +1 757-751-0347 Hampton, VA 23666, United States
ReplyDeleteVery good blog! if you have any questions related to their Quickbooks Software then contact our team at Quickbooks customer service Plymouth , United States+18664486293
ReplyDeleteWow another very good knowledge Thanks for the great information. And it’s quite useful.
ReplyDeletedivorce records new jersey
ERP TRAINING NOIDA is a premier institute for SAP MM training in Noida that offers high-quality training and placement assistance to aspiring SAP MM professionals. With its experienced trainers, unique training methodology, and flexible training schedules, ERP TRAINING NOIDA is the perfect destination for students who want to take their SAP MM career to the next level.
ReplyDeleteThis is a very informative article on Windows PowerShell remoting and host-based firewall configuration. I learned a lot from reading it. I also appreciate the links to the online exam help resources. They are very useful for students who want to prepare for the certification exams. Thank you for sharing your knowledge and expertise.
ReplyDeleteI am impressed by your detailed explanation of Windows PowerShell remoting and host-based firewall configuration. You have a great command of the topic and you presented it in a clear and concise way. I found the online paper help resources very helpful as well. They helped me to review the concepts and practice the skills. I am grateful for your generosity and professionalism.
ReplyDeleteIf you are looking for online help about QuickBooks then you need to need to dial QuickBooks customer service +1 877-755-5046 that number for your queries and errors issues.
ReplyDeleteGreat Blog! In Case when you are Facing some Unexpected technical Issue then get the best technical solutions for QuickBooks queries. call us on Quickbooks customer service +1 347-982-0046
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteQuickBooks also offers Quickbooks customer service If you need help with your QuickBooks account, call the +1 855-604-1500 customer service number above.
ReplyDeleteQuickBooks is amazing software is best choice of your business if you are looking growth of their company call us on
ReplyDeleteQuickBooks customer service +1 855-377-7767
QuickBooks- Accounting software is very popular accounting . ! . If you want to get in touch with your QuickBooks Expert then Dial QuickBooks customer service +1 602-362-8345
ReplyDeleteAncient civilizations, such as body to body massage near me the Egyptians, Greeks, and Romans, developed elaborate bathhouses and hot springs
ReplyDeleteLong Strokes: Balinese Massage uses female to male massage centre near me long and gliding strokes to warm up the muscles and prepare the body for deeper work.
ReplyDeletevery good content ! If you need help with your account or just have any other questions about QuickBooks then call at
ReplyDeleteQuickBooks Customer Service Phone Number +1 877-755-5046
If you are QuickBooks User. If you're looking for QuickBooks help then
ReplyDeleteQuickBooks Customer Support +18559411563 for every problems
QuickBooks is a software program that was developed by Intuit. If you are looking for help with QuickBooks or any other accounting software contact them on the QuickBooks Customer Service+17577510347
ReplyDeleteExcellent weblog, many thanks a lot for your awesome posts! leer mas
ReplyDeleteour web site sclinbio,com
Explore the world of soothing female to male body massage at home treatments to couples' sessions, discover the perfect massage center for you.
ReplyDeleteExcellent weblog, many thanks a lot for your awesome posts! leer mas
ReplyDeleteour web site https:/sclinbio,com/
best service body massage near me
ReplyDeleteThe product must meet the Indian Standard Specification criteria.
ReplyDeleteBIS license is only given to the factory (manufacturer of finished products), not to the Distributor/Retailer.
If a manufacturer has multiple factories, each of which is located at a distinct geographical address, the business must file a separate application for each product and factory location.
The laboratory should be fully equipped with product testing equipment as well as qualified quality control personnel to test the product in accordance with the applicable ISS.
All production machinery and testing facilities should be located on the factory premises as per ISS norms and respective SIT.
All procedures should be completed in the same factory, from receiving raw materials to final packing. If any out-sourcing is required, clearance from the Bureau may be requested.
The technical guidelines are available for all products covered under the Product Certification Scheme as 'Product Manuals'. Product manuals include sampling guidelines, a list of test equipment, a Scheme of Inspection and Testing (SIT), a description of scope etc. Applicant can refer to this Product Manual for BIS ISI Certification to prepare for the audit and application submission so that chances of rejection can be avoided.
Benefits of BIS Certification (ISI Mark Certificate)
With ISI Mark Certification, companies and their products simply unlock the following motives:
ISI Consultants
BIS Certification
BIS ISI Registration Consultants
BIS ISI Mark Registration Certification
ISI Mark Certificate allows the manufacturers uninterrupted manufacturing and selling of their products in every part of India.
BIS certification allows the manufacturers to use the Standard Mark i.e, ISI Mark on their manufactured products that are in the mandatory certification scheme. Manufacturing these products without an ISI Mark could result in a substantial fine, imprisonment or both.
ISI Mark on any product ensures consumer's safety and health and develops trust.
BIS certified product ensures high quality and consumer satisfaction, which increases revenue.
Do you know that ISI Mark Certification is mandatory in India for more than 150 products? Even though it is voluntary to get BIS license, the BIS made it compulsory to attain the certificate on certain products to make sure the safety of the consumers from counterfeits and fake merchandise.
Trusted Abogado De Trafico en Virginia will provide you a legal advice with a representation.
ReplyDeleteNice Blog, Thanks for sharing with us! Keep Sharing.
ReplyDeleteDo you want to buy Resistive Touch Monitors online at affordable rate?
Buy Resistive Touch Monitors
Very interesting Blog ! If you are looking Expert in QuickBooks Issue ? then you you can dial QuickBooks Customer Service +1 877-606-0004 and talk to someone who will help you out through live chat.
ReplyDeleteCombining acupressure body massage near me energy balance, it goes beyond the superficial, delving into the core of physical and mental well-being.
ReplyDeleteFantastic blog. Reading your articles was enjoyable. For me, this is a very fantastic read. I've bookmarked it and am eager to read the newest pieces. Continue your fantastic effort!
ReplyDeleteData science training institute in KPHB
Embark on the journey of turning raw data into actionable insights for unparalleled channel growth. Master the intricacies of YouTube analytics, decoding the language of watch times, engagement metrics, and click-through rates. Each data point is a compass guiding the refinement of your content strategy. Analyze audience behavior to tailor your content, ensuring it resonates deeply. With every insight gained, optimize your channel for sustained growth, evolving in tandem with audience preferences. In the realm of data-driven decisions, the power to transform analytics into action propels your content toward continuous and lasting success on YouTube.
ReplyDeletehttps://www.buyyoutubesubscribers.in/
pune is top city in maharastra in this hectic life people will need body to body massage in pune for over come the tensions and relaxing issues.
ReplyDeleteLASIK surgery in Delhi offers a transformative experience, blending meticulous care with the latest in laser vision correction technology. Patients access world-class expertise and undergo a life-altering procedure that diminishes reliance on glasses or contacts. Tailored treatments and rigorous safety protocols underscore the city's commitment to vision excellence. Affordable yet uncompromising on quality, Delhi’s LASIK procedures are a beacon for those seeking clearer sight. The city has become synonymous with reliable, state-of-the-art corrective eye surgery.
ReplyDeletehttps://www.visualaidscentre.com/lasik-eye-surgery/
Expand your YouTube horizons by purchasing genuine subscribers. By investing in a real audience, you nurture an environment ripe for active engagement — comments, likes, and pertinent discussions that propel your content through the YouTube algorithm. Every legitimate subscriber adds a stone to the foundation of your expanding community, each interaction a step closer to enhanced organic visibility. Harness the power of authenticity with subscribers who care about your content and become ambassadors of your brand. With each new real subscriber, your digital footprint widens, bringing your message to even more eyes. Make a lasting impact by coupling this with continuous delivery of compelling content, and watch as your channel evolves into a flourishing digital ecosystem.
ReplyDeletehttps://sites.google.com/view/buyytsubscribers/
Transform your channel with our specialized service to buy YouTube views in India, a strategy specifically tailored to amplify your online presence among Indian audiences. Enjoy a significant uptick in viewership with genuine, YouTube-compliant views that elevate your content's appeal. Tailored to the dynamism of the Indian market, our service offers a safe and impactful means to boost your visibility and captivate a vast and diverse viewership. Witness your videos garner attention, influencing higher engagement rates and enhancing the potential of going viral within the Indian community. Our commitment to authenticity ensures that every view counts towards building a credible and growing fan base. Harness the power of targeted growth and set your channel on the path to becoming a prominent name among the Indian YouTube ecosystem.
ReplyDeletehttps://www.buyyoutubeviewsindia.in/
Leap into the digital age with our Cheap Website Hosting, a haven for cost-conscious creators seeking to claim their space online. Our service prioritizes affordability without skimping on quality, offering generous storage, robust security, and unwavering uptime. Quick-loading servers located domestically ensure a smooth, responsive experience for your visitors. Support is always at the ready, ensuring any hiccups are resolved without delay. Perfect for start-ups and bloggers, our hosting solution is your budget-friendly ticket to online visibility. Step up your digital game with Cheap Website Hosting—an investment in reliability at a fraction of the cost.
ReplyDeletehttps://onohosting.com/
Introduce a game-changing element to your YouTube channel with our 'Buy Active YouTube Views' service. A strategic tool designed to turbocharge your channel's organic growth and visibility. By attracting authentic and engaged viewers, we enhance your content's reach, fostering potential collaborations. Our service is acclaimed for its safety and efficiency. Embrace the power of active views and watch your YouTube channel skyrocket amidst the competitive online video platform.
ReplyDeletehttps://www.buyyoutubeviewsindia.in/
Affordable web hosting in India caters to the thrifty yet ambitious web entrepreneur, offering a suite of features that defy the modest cost. These hosting services provide reliable performance, with adequate server uptime and bandwidth, making sure that websites are always operational and swift. The inclusion of user-friendly control panels and one-click installations for popular CMS platforms lowers the technical barriers for beginners. Even on a shoestring budget, customers receive attentive support and sufficient resources to foster their online venture's growth.
ReplyDeletehttps://onohosting.com/
This comment has been removed by the author.
ReplyDeleteIn the digital realm of Indian YouTube channels, the temptation to buy subscribers is a shortcut fraught with complications. It promises a swift surge in numbers, potentially luring more organic followers through the illusion of popularity. However, these purchased subscribers rarely engage, rendering the spike in numbers virtually meaningless and not reflective of an engaged audience. Despite the perceived quick fix, this practice breaches YouTube's policies, endangering a channel's legitimacy and existence. Creators are advised to cultivate genuine connections, prioritizing content quality over deceptive metrics to nurture a truly devoted viewership.
ReplyDeletehttps://buyyoutubesubscribersindia.weebly.com/
In India, the act of buying Google reviews is a practice frowned upon for its ethical breaches and stark violation of Google's policies. Underpinned by a desire to unjustly enhance a business's online presence, this method involves paying for falsified reviews to sway public opinion and inflate perceived trustworthiness. Such tactics, while temporarily uplifting a business's online ratings, can have deleterious long-term effects, including punitive actions by Google and erosion of genuine customer loyalty. Discerning consumers in India's vibrant marketplace often seek out authentic experiences and can feel misled by manipulated reviews, ultimately leading to diminished brand reputation. It is imperative that businesses focus on organic growth, inviting real feedback rooted in customer satisfaction, which stands as a cornerstone of sustainable success in India's digital economy.
ReplyDeletehttps://www.seoexpertindelhi.in/buy-google-reviews/
Indian nurses in Singapore are integral to a healthcare system that marries compassion with cutting-edge practices. They receive competitive pay, engage in continuous professional development, and enjoy structured career advancement. By working within world-class facilities and a multicultural environment, they expand their clinical expertise and cultural sensitivities. It is a landscape where Indian nurses don't just evolve professionally but also contribute to a globally recognized standard of healthcare. They are welcomed into a setting that values their dedication and supports their well-being, crafting careers that are both impactful and fulfilling.
ReplyDeletehttps://dynamichealthstaff.com/nursing-jobs-in-singapore-for-indian-nurses
Experience the perfect blend of affordability and quality with India's top affordable web hosting services. Designed with both the budding entrepreneur and the established business in mind, these hosting solutions offer an economical yet reliable online presence. Enjoy features like generous storage, unlimited bandwidth, and 24/7 customer support, ensuring your website's performance is never compromised. With an impressive 99.9% uptime guarantee and user-friendly control panels, even beginners can navigate the digital space with ease. Start your online journey confidently with a host that prioritizes your growth and your budget.
ReplyDeletehttps://hostinglelo.in/
For business owners in India seeking enhanced online reputation and visibility, ReviewsRamp.com stands out as the premier destination for purchasing Google reviews. Not only do they prioritize quality and authenticity in every testimonial, but their service is also designed to be seamless and economical. At ReviewsRamp.com, companies can acquire valuable feedback that reflects real-world customer experiences, providing a boost that's both genuine and strategic. With the intent to improve search engine rankings subtly and securely, ReviewsRamp.com offers an exceptional service that equates to a wiser investment for long-term digital credibility and success.
ReplyDeletehttps://www.sandeepmehta.co.in/buy-google-reviews/
Grow Your Fanbase: Buy Spotify Followers and Expand Your Reach! In the competitive world of music streaming, building a loyal fanbase is essential. With the option to purchase Spotify followers, you can kickstart your journey to success. Increase your credibility and visibility on the platform, attracting more organic followers in the process. Investing in followers not only boosts your social proof but also improves your chances of getting noticed by curators and influencers. Don't let your talent go unnoticed—take action today. Buy Spotify followers and watch your fanbase flourish, leading to more streams, engagements, and opportunities. With a strategic approach, you can accelerate your music career and stand out in the crowd. Don't wait for your breakthrough; make it happen with Spotify followers.
ReplyDeletehttps://www.spotifyfame.com/
Boost Your Channel: Buy Twitch Channel Views and Increase Your Visibility! In the bustling world of Twitch, gaining exposure is essential for growth. Enhance your credibility and attract more viewers by purchasing Twitch channel views. With each view, you amplify your presence and attract potential followers to your streams. Take charge of your streaming journey today and invest in expanding your Twitch channel views. Buying views not only accelerates your channel's visibility but also opens doors to exciting opportunities within the streaming community. Don't let your content go unnoticed—amplify your impact and leave a lasting impression. With strategic promotion, you can cultivate a dedicated fanbase and establish yourself as a standout creator. Don't wait for recognition; seize it with the influence of Twitch channel views.
ReplyDeletehttps://twitchviral.com/
Unlock Your Video's Potential: Buy YouTube Views Online and Elevate Your Reach! In the vast expanse of YouTube, visibility is key to success. Boost your video's credibility and attract more viewers by purchasing YouTube views online. With each view, you enhance your video's visibility and appeal, drawing in organic traffic. Take control of your content's trajectory today and invest in expanding your YouTube views conveniently online. Buying views not only accelerates your growth but also opens doors to new opportunities within the platform's algorithms. Don't let your content get lost in the shuffle—amplify its impact and captivate your audience. With strategic promotion, you can establish a formidable presence and elevate your channel's reputation. Don't wait for recognition; seize it with the influence of YouTube views purchased conveniently online.
ReplyDeletehttps://sites.google.com/site/buyytviewindia/
Looking to enhance your Spotify experience with premium plays? Consider purchasing Spotify premium plays today! Increasing your play count with premium streams not only boosts your tracks' visibility but also supports artists with higher royalties. With premium plays, your music gains exposure to a wider audience, leading to increased recognition and potential for success. Investing in Spotify premium plays is a strategic move to accelerate your music career and stand out in the competitive streaming landscape. Skip the generic plays and opt for premium streams for maximum impact and authenticity. Don't miss out on the opportunity to reach more listeners who appreciate quality music. Buy Spotify premium plays now and watch your tracks soar to new heights of success!
ReplyDeletehttps://www.spotifyfame.com/
Looking to boost your Twitch channel's visibility without breaking the bank? Consider purchasing cheap Twitch followers today! Increasing your follower count affordably not only enhances your channel's credibility but also attracts more viewers and engagement. With cheap followers, you can kickstart your journey to Twitch success without spending a fortune. Investing in cheap Twitch followers is a strategic move to stand out from the competition and accelerate your channel's growth. Skip the expensive marketing tactics and opt for an affordable solution. Don't miss out on the opportunity to maximize your channel's reach while saving money. Buy Twitch followers cheap now and watch your channel's popularity soar!
ReplyDeletehttps://twitchviral.com/
Looking to skyrocket your YouTube video's visibility instantly? Consider investing in instant YouTube views today! Boosting your view count in an instant not only enhances visibility but also establishes credibility and attracts organic growth. With instant views, your videos gain immediate traction and attract attention from a broader audience, leading to accelerated success on the platform. Investing in instant YouTube views is a strategic move to gain an immediate competitive edge and stand out from the crowd. Skip the slow process of building views organically and opt for rapid growth to propel your channel forward. Don't miss out on the opportunity to maximize your video's reach and impact instantly. Buy instant YouTube views now and watch your videos soar to new heights of popularity immediately!
ReplyDeletehttps://sites.google.com/site/buyytviewindia/
The pressure applied in a massage may improve blood circulation. This can then transfer oxygen and nutrients to cells in a more efficient manner and improve overall well-being and health.
ReplyDeleteb2b spa in chennai
Embark on a journey to clarity with Silk Eye Surgery in Delhi, where precision meets luxury. Unveil a world of vivid sights without compromise. Experience the pinnacle of ocular refinement, as skilled surgeons weave their expertise into the fabric of Silk Eye Surgery. In the heart of Delhi, discover a vision transformation that transcends expectations. Amidst the bustling cityscape, the cost of this exquisite procedure is a testament to affordability and excellence. Elevate your gaze with Silk Eye Surgery, a symphony of skill and silk, crafting a tapestry of visual brilliance. Unravel the mysteries of clear vision at a cost that resonates with both quality and value. Delhi awaits, adorned with the silk touch of refined eye care.
ReplyDeletehttps://medium.com/@pojagupta/silk-eye-surgery-elita-860c70c593ad
Unleash the power of a confident smile with Smile Pro Laser Vision Correction. Bid farewell to glasses and contacts as cutting-edge technology transforms your vision. Precision meets perfection as the laser corrects your eyes, paving the way for a life without visual limitations. Experience the freedom to embrace every moment, unencumbered by the hassle of corrective eyewear. Smile Pro ensures a painless, quick procedure, leaving you with sharper, clearer vision. Say goodbye to squinting and hello to a world seen through a new lens of clarity. Let your smile reflect the joy of newfound visual freedom, brought to you by Smile Pro Laser Vision Correction. See the world with confidence, and let your eyes sparkle with the radiance of a life unburdened.
ReplyDeletehttps://smileproeyesurgery.medium.com/smile-pro-eye-surgery-in-delhi-fbafc721a9ce
In the bustling heart of Delhi, the Smile Pro Eye Doctor stands as a beacon of optical expertise and genuine care. With a commitment to vision wellness, this esteemed eye clinic combines cutting-edge technology with a warm smile-centric approach. Expert optometrists and ophthalmologists work in harmony to provide personalized solutions, ensuring each patient leaves with a brighter outlook. From comprehensive eye exams to advanced treatments, the Smile Pro team crafts a tailored experience for every individual. Nestled in the city's vibrant landscape, their state-of-the-art facility redefines eye care. Trust Smile Pro for a vision journey that goes beyond sight – where professionalism meets compassionate smiles, delivering unparalleled optical care to Delhi's discerning residents.
ReplyDeletehttps://www.linkedin.com/pulse/smile-pro-eye-surgery-delhi-romila-chaudhary-y5imc/
Embark on a journey to rejuvenate your eyes with Silk Eye Surgery in Delhi. Our state-of-the-art procedure combines precision and luxury for a truly seamless experience. Bid farewell to wrinkles, sagging skin, and tired eyes as our skilled surgeons work their magic. Discover a world where beauty meets innovation, offering you the gift of youthful, silk-smooth eyes. With our cutting-edge technology and personalized care, Silk Eye Surgery in Delhi is the ultimate solution for a brighter, more vibrant gaze. Trust us to unveil a new era in eye aesthetics, where each procedure is tailored to enhance your natural allure. Elevate your look, enhance your confidence – choose Silk Eye Surgery for timeless beauty.
ReplyDeletehttps://medium.com/@pojagupta/silk-eye-surgery-elita-860c70c593ad
Discover the liberating power of Smile Pro Specs Removal Surgery, a life-changing solution for visual freedom. Bid farewell to glasses and embrace a world of clarity with confidence. Our advanced procedure offers a safe and effective way to correct vision impairment. Experience the joy of waking up to clear vision every day, without the hassle of glasses. Smile Pro Specs Removal Surgery is a testament to technological innovation and precision. Trust in our expertise to unlock a brighter, lens-free future for your eyes. Elevate your lifestyle and see the world in crystal-clear detail with Smile Pro.
ReplyDeletehttps://www.linkedin.com/pulse/smile-pro-eye-surgery-delhi-romila-chaudhary-y5imc/
Embark on a journey to radiant smiles with Smile Pro in India, setting a new standard for dental care. Our state-of-the-art clinics combine cutting-edge technology and experienced professionals to ensure your dental health is in expert hands. From teeth whitening to advanced cosmetic dentistry, Smile Pro offers personalized solutions for every smile. Embrace confidence in your grin with our comprehensive dental services, bringing world-class oral care to your doorstep. With Smile Pro, rediscover the joy of smiling, knowing your dental wellness is our top priority. Join the countless satisfied clients who have transformed their smiles with precision and care. Experience the future of dentistry with Smile Pro, making India smile brighter, one person at a time.
ReplyDeletehttps://smileproeyesurgery.medium.com/smile-pro-eye-surgery-in-delhi-fbafc721a9ce
Elevate your celebrations with our premier trophy-making company. Crafted excellence meets bespoke design as we bring your vision to life. From sports triumphs to corporate achievements, our trophies embody prestige and quality. Entrust your milestones to our skilled artisans, ensuring each piece reflects the significance of your success. As a leading trophy-making company, we merge tradition with innovation, delivering timeless awards that inspire pride. Let us be the architects of your recognition, creating trophies that stand as symbols of accomplishment. Choose distinction, choose our trophy-making expertise for a lasting mark of excellence.
ReplyDeletehttps://www.angelstrophies.com/
Navigating the complexities of divorce? Seek guidance from a Mutual Divorce Lawyer in Delhi. Our seasoned legal experts specialize in amicable separations, ensuring a smooth transition for both parties. With empathy and professionalism, we strive to resolve disputes with mutual understanding and respect. Trust in our expertise to protect your interests and facilitate a fair settlement. As your advocates, we're committed to simplifying the legal process and providing clarity every step of the way. Let us guide you through this challenging time with compassion and expertise. Choose a Mutual Divorce Lawyer in Delhi for a seamless transition to your next chapter.
ReplyDeletehttps://bestdivorcelawyerindelhi.com/
Join top-rated React Training in Hyderabad to boost your web development skills. Interactive sessions, real-world projects, and expert instructors. Enroll now.
ReplyDeleteElevate your recognition with the finest awards crafted by our prestigious manufacturer. Each trophy is meticulously designed to embody excellence and honor achievements. From sleek corporate awards to intricate sports trophies, we tailor every piece to perfection. Our dedication to quality ensures that your accolades shine as brightly as your accomplishments. Trust in our craftsmanship to capture the essence of success in every detail. Partner with the leading awards manufacturer and celebrate your achievements with distinction.
ReplyDeletehttps://www.angelstrophies.com/
In the vibrant heart of Mumbai, an eminent Breast Cancer Surgeon is revolutionizing the approach to battling breast cancer with unmatched expertise and a deeply compassionate touch. Her innovative surgical techniques, combined with a meticulous emphasis on personalized patient care, set her apart in the field of oncology. Known for blending cutting-edge technology with a holistic approach to treatment, she ensures every patient not only receives the best medical care but also the emotional and psychological support needed during their healing journey. Her advocacy for early detection and patient education underscores a proactive stance against breast cancer, making her a vanguard in her field. Through community outreach and awareness programs, she extends her influence beyond the clinic, championing the cause of breast cancer prevention and care. Her practice stands as a beacon of hope, where patients find not just a doctor, but an ally in their fight against breast cancer, embodying the perfect synthesis of medical excellence and heartfelt compassion.
ReplyDeletehttps://drnitanair.com/
Navigate through challenging times with the expertise of the best divorce advocate in Delhi by your side. Our experienced legal team offers compassionate guidance and strategic counsel tailored to your unique situation. With a focus on resolution and protection of your interests, we strive for optimal outcomes. Trust in our track record of success and commitment to your well-being throughout the process. Whether it's mediation, litigation, or collaborative divorce, we are your steadfast allies. Rest assured, your case will be handled with professionalism and discretion, ensuring a smoother transition. Choose peace of mind, choose the best divorce advocate in Delhi to guide you towards a brighter tomorrow.
ReplyDeletehttps://bestdivorcelawyerindelhi.com/
Embark on an exciting career journey with an Ireland Nursing Recruitment Agency in India. Our agency specializes in connecting skilled Indian nurses with rewarding opportunities in Ireland's esteemed healthcare sector. With personalized assistance and guidance, we streamline the recruitment process for you. Say goodbye to uncertainties and let us pave the way for your successful transition abroad. Explore the beauty of Ireland while making a meaningful impact in healthcare. Trust our expertise to match you with the perfect nursing position tailored to your qualifications and aspirations. Join hands with us today and step into a future filled with professional growth and cultural enrichment.
ReplyDeletehttps://suntechhealthcarepro.com/ireland-nurses-recruitment-agency-in-india/
In the vibrant city of Ahmedabad, a distinguished Liver Cancer Specialist shines as a luminary in the realm of oncological care. This expert, renowned for their innovative approach, combines the latest in medical advancements with compassionate patient care to offer a beacon of hope to those facing liver cancer. With a relentless commitment to excellence and patient well-being, they leverage state-of-the-art diagnostic and treatment techniques to customize care for each individual. Beyond their clinical achievements, they dedicate themselves to educating the community on liver health, emphasizing the importance of prevention and early intervention. This specialist's tireless work not only elevates the standard of healthcare in Ahmedabad but also inspires a future where liver cancer can be confronted more effectively and compassionately.
ReplyDeletehttps://drvirajlavingia.com/
Situated in the bustling city of Gurgaon, the Breast Cancer Surgeon is a true luminary in the realm of oncological surgery. With a talent for blending surgical expertise with compassion, they work tirelessly to offer the best outcomes for their patients. This surgeon employs state-of-the-art surgical methods aimed at not only treating cancer but also preserving the quality of life. Their competence in using the latest technologies and techniques marks a significant leap towards innovative cancer care. The doctor's patient-first philosophy ensures personalized care plans, nurturing trust and comfort. Beyond the skillful handling of medical instruments, their warmth and empathy encapsulate the essence of holistic healing. Each successful surgery is not just a physical recovery but a restoration of hope. The Breast Cancer Surgeon in Gurgaon stands as a beacon, guiding patients through their darkest hours with unparalleled dedication and medical prowess.
ReplyDeletehttps://www.breastoncosurgery.com/
Thank you very much for your wonderful blogs!Abogado de DUI Condado de Prince William
ReplyDeleteBased in Australia, our SEO agency is a vanguard of digital marketing excellence, specializing in elevating brands to premier online positions. Our approach is holistic, blending state-of-the-art SEO practices with innovative content strategies to optimize search engine visibility. Our core services include detailed keyword analysis, strategic link building, and comprehensive on-page and off-page optimization, tailored to fit each client's unique digital landscape. We are dedicated to not only improving search engine rankings but also enhancing user experience, driving meaningful traffic that converts. Our team, comprised of industry veterans, employs cutting-edge tools and data analytics to ensure every strategy is backed by solid research and real-world results. We prioritize transparent communication, ensuring our clients are always informed and involved in the decision-making process. With a proven track record of success, we stand as a leading SEO agency in Australia, committed to propelling businesses forward in the digital age.
ReplyDeletehttps://digiquakesolutions.com/
Looking to boost your YouTube channel's visibility? Buy YouTube Subscribers Cheapest in India and expand your audience effortlessly. Our service offers real subscribers at the most competitive prices in the Indian market. Gain instant credibility and increase your channel's reach with our affordable subscriber packages. Don't compromise on quality; our subscribers are genuine and active users. Elevate your online presence and stand out among the competition with our reliable service. Unlock the potential for exponential growth and maximize your channel's success today. Invest wisely in your YouTube journey and watch your subscriber count soar. Buy now and take the first step towards YouTube success!
ReplyDeletehttps://www.theweek.in/news/biz-tech/2022/07/07/buy-youtube-views-and-grow-your-business-in-2022.html/
Looking to grow your YouTube channel organically? Buy Legit YouTube Subscribers from our trusted service. Our subscribers are real and active, ensuring genuine engagement with your content. Say goodbye to fake accounts and bots; we deliver authenticity and reliability. Boost your channel's credibility and reach new audiences effectively. With our secure and transparent process, you can trust in the quality of our subscribers. Expand your subscriber base ethically and watch your channel thrive. Invest in legitimate growth and see real results today. Don't wait any longer—take your YouTube journey to the next level now!
ReplyDeletehttps://www.deccanherald.com/brandspot/pr-spot/buy-youtube-views-subscribers-the-company-that-is-churning-successful-youtube-stories-one-after-another-1118911.html/
Ready to take your YouTube channel to the next level? Buy Legit YouTube Subscribers and watch your audience grow authentically! Our service offers genuine subscribers who will engage with your content, boosting your credibility and visibility. Say goodbye to fake accounts and bots; we deliver real subscribers that enhance your channel's reputation. Gain traction and increase your reach with our trustworthy subscriber packages. Don't compromise on authenticity when it comes to building your subscriber base. Invest in legitimate growth and see the difference it makes in your channel's success. Buy now and elevate your YouTube presence with real, active subscribers who genuinely enjoy your content.
ReplyDeletehttps://www.deccanherald.com/brandspot/pr-spot/buy-youtube-views-subscribers-the-company-that-is-churning-successful-youtube-stories-one-after-another-1118911.html/
Enhance your YouTube channel's impact now! Buy High-Quality YouTube Subscribers to elevate your online presence. Our service guarantees genuine subscribers who actively engage with your content, fostering organic growth. Experience an increase in credibility and visibility with every authentic subscriber gained. Don't settle for quantity over quality – invest in subscribers who truly value your channel. With our reliable service, expect premium results without compromising authenticity. Don't miss the chance to propel your channel to new heights. Purchase today and witness the power of high-quality subscriber acquisition!
ReplyDeletehttps://www.theweek.in/news/biz-tech/2022/07/07/buy-youtube-views-and-grow-your-business-in-2022.html/
Looking to accelerate your YouTube growth? Explore our Buy YouTube Subscribers Services for instant channel expansion. Gain genuine subscribers who actively engage with your content, boosting your credibility and visibility. Skip the slow grind and invest in reliable subscriber acquisition services. With our expertise, you'll see rapid results without compromising authenticity. Elevate your channel's success and stand out in the competitive YouTube landscape. Say goodbye to stagnant growth and hello to a thriving subscriber base. Invest in your YouTube journey today with our trusted services. Buy now and watch your channel flourish!
ReplyDeletehttps://www.aninews.in/news/business/business/viral-promotions-the-company-that-has-created-stars-out-of-youtubers20230328182117/
Nice Blog. Thanks for sharing with us. Keep Sharing.
ReplyDeleteDo you want to Buy High Brightness IR Touch Monitors Online?
Buy High Brightness IR Touch Monitors
Looking to increase your YouTube subscribers without breaking the bank? Look no further! Buy YouTube Subscribers Cheapest in India from us and boost your channel's visibility at an unbeatable price. Our affordable packages offer real subscribers, ensuring genuine engagement and organic growth for your content. Say goodbye to expensive marketing campaigns and hello to cost-effective solutions that deliver results. With our reliable service, you can trust in the quality of your subscriber base. Expand your audience and maximize your channel's potential without draining your budget. Don't miss out on this opportunity to elevate your YouTube presence affordably. Invest in the cheapest YouTube subscribers in India today and watch your channel flourish with increased views and interactions. Unlock the power of affordable growth and achieve your YouTube goals without overspending.
ReplyDeletehttps://www.theweek.in/news/biz-tech/2022/07/07/buy-youtube-views-and-grow-your-business-in-2022.html
Looking to boost your YouTube presence? Buy high-quality YouTube subscribers today and skyrocket your channel's visibility. Our genuine subscribers are real users who engage with your content, enhancing your credibility and reach. Gain instant credibility and attract more organic viewers with our reliable subscriber service. Don't waste time waiting for growth - kickstart your success with our hassle-free solution. We offer a variety of packages to suit your needs, ensuring maximum impact for every budget. Elevate your channel to new heights and join the ranks of successful content creators. Don't miss out on this opportunity to become a YouTube sensation - buy high-quality subscribers now!
ReplyDeletehttps://www.theweek.in/news/biz-tech/2022/07/07/buy-youtube-views-and-grow-your-business-in-2022.html
Shravan Tech is committed to providing accurate and authentic information through its Hindi blogging platform. Our diverse team of graduates focuses on providing timely and relevant technical insight and advice.
ReplyDeleteThe hunt for the offender grew more intense as the days stretched into weeks. Social media was inundated with public requests for information, pleading with anyone who had any knowledge of the incident to come forward. The public's indignation spurred authorities to pursue justice vigorously, turning over no stone in their effort to hold the offender accountable for their deeds.fairfax hit and run
ReplyDeleteThanks for Sharing. Google Video Search allows users to find video content across the web efficiently. By leveraging Google's powerful algorithms, it delivers highly relevant results from various sources, including YouTube. This tool enhances content discovery, making it easier for users to access specific video information quickly.
ReplyDeleteWonderful experience while reading your blog.
ReplyDeleteplaces to visit in Dubai
Uae Tour Packages
Sharjah Tour Packages
If you are looking for the best spa services in chennai for female to male body spa services then you have made the right choice through our website, you can get a wide range of spa treatments and tips from our center for ultimate relaxation and wellness.
ReplyDeleteRay Mackay is a seasoned expert in online research skills course, offering invaluable insights and training for those looking to enhance their research abilities in the digital age. With extensive experience in the field, Ray specializes in equipping professionals, students, and researchers with the essential tools and techniques to navigate the vast landscape of online information effectively. His online research skills course is designed to cover everything from advanced search strategies to critical evaluation of online sources, ensuring that participants gain practical skills that significantly boost their research efficiency and accuracy.
ReplyDelete
ReplyDeleteExciting update with Android 7.0 Nougat on Moto phones! For business insights, explore practising company secretary in Coimbatore.
This is good of Social media was inundated with public requests for information.
ReplyDeleteNeed reliable Windows hosting? Webyne Windows Hosting delivers powerful, scalable, and cost-effective solutions for businesses, ensuring high performance and security.
ReplyDelete"Egypt offers affordable MBBS programs with globally recognized degrees. Its medical universities provide quality education, experienced faculty, and diverse clinical exposure. With lower tuition fees and modern facilities, Egypt is becoming a popular destination for international medical students."
ReplyDeleteMbbs in Egypt
The Padded Bra offers extra comfort and a natural lift, enhancing your shape while providing a smooth, seamless fit. It's perfect for everyday wear, offering support and style in one. Ideal for confidence and all-day comfort.
ReplyDeletePADDED BRA
Good one !!! nuru massage
ReplyDeleteNice post !!! bodymassageinchennai
ReplyDeleteA sports bra is designed to provide support, comfort, and stability during physical activities, reducing strain on the bust. It's typically made from moisture-wicking, breathable fabrics, offering a snug fit that minimizes movement and enhances performance in sports, exercise, and high-impact workouts. Perfect for athletes and fitness enthusiasts, it promotes comfort and confidence, allowing for unrestricted movement and reduced discomfort during intense activity. Available in various styles and support levels to cater to different needs and preferences.
ReplyDeletePADDED BRA
Pursuing an MBBS in Uzbekistan has become an attractive option for international students, especially those from India, Pakistan, Bangladesh, and other countries looking for affordable yet high-quality medical education. Uzbekistan offers globally recognized medical degrees, experienced faculty, and modern infrastructure at a fraction of the cost compared to Western countries.
ReplyDeleteMBBS in Uzbekistan
Thanks for the insightful guide on PowerShell Remoting! Super useful for security! To find more visit my website.
ReplyDeleteI absolutely love this idea! A travel jewelry organizer is such a game-changer, especially for those of us who are constantly on the go. It's so frustrating trying to untangle necklaces or scramble to find matching earrings in a suitcase. I love how these organizers keep everything neat and easily accessible—no more mess or stress! Plus, the designs are super stylish, which makes it feel like you're not just keeping your jewelry safe, but also adding a touch of elegance to your travels. Definitely adding one of these to my packing essentials!
ReplyDeletetravel jewellery organiser
You’ve done an excellent job breaking down a complex issue. I now feel much more confident about this topic.
ReplyDeleteGreat insights on the latest business trends in the Middle East! The region continues to grow with exciting opportunities, especially in tech and innovation. Looking forward to more updates on how businesses are adapting to these changes. Keep it up!
ReplyDeleteMiddle East business news updates
This party wear clutch is absolutely stunning! The design is elegant and the perfect accessory to complete any outfit. Whether it's a formal event or a night out, this clutch adds a touch of glamour. Highly recommend!
ReplyDeleteParty Wear Clutch
Its starts in a bath tub, where you lay down and the masseuse will give you such a bath that even you would not have taken it in your entire life. She will clean you from your head to toe along with nuru massage in chennai. You must have learned from your childhood that you should take extra care of your private parts, so has she, masseuse will do that for you also. She will bath you and herself in the tub. The fun just started.
ReplyDeleteThanks for sharing this information with us and it was a nice blog.Healthcare IT Solutions
ReplyDeleteMake your online dream a reality for ₹999.
ReplyDeletewebsiteunder999.com delivers full website setup — hosting, and design — all included.
No tech skills needed!
Nice Blog. Thanks for sharing with us.
ReplyDeleteBuy Curved PCAP Touch Monitors with LED Lights
Luxury Living in Jaipur – A Royal Lifestyle Redefined
ReplyDeleteStep into a world where heritage elegance meets modern sophistication. Luxury living in Jaipur offers an exceptional blend of timeless architecture, spacious residences, and state-of-the-art amenities. Whether nestled in serene gated communities or standing tall as contemporary penthouses, these homes reflect the regal spirit of the Pink City while catering to the lifestyle demands of today’s discerning homeowner.
Luxury Living in Jaipur
The SF139E is a thermal cutoff (TCO) fuse manufactured by NEC SEFUSE, designed to provide over-temperature protection in a wide range of electrical and electronic devices. It is a one-shot, non-resettable safety component that acts as the last line of defense in case of excessive heat buildup. Once activated, it interrupts the electrical circuit permanently to prevent potential hazards such as fire, smoke, or damage to sensitive components.
ReplyDeleteSF139E SEFUSE thermal cutoff
This is a valuable blog for manufacturers and exporters! I came across a great resource on BIS Scheme X Certification that clearly explains the procedure, timelines, and document requirements.
ReplyDeleteGreat insights on digital marketing courses! The way you explained the scope, career opportunities, and practical training benefits is very helpful for beginners planning their career in this field.
ReplyDeleteDigital Marketing Course In Hyderabad.
Elwin Hessel, a wellness enthusiast passionate about natural healing and holistic care. If you’ve been searching for an effective way to soothe aches and discomfort without harsh chemicals, the herbal pain relief lotion from Tru Releaf is a game changer. This all-natural formula blends premium herbal extracts and essential oils designed to deliver fast, deep relief for sore muscles, stiff joints, and everyday body pain. Unlike synthetic creams, this herbal pain relief lotion works with your body’s natural healing process to reduce inflammation, ease tension, and restore comfort. Its lightweight, non-greasy texture absorbs quickly, leaving your skin nourished and refreshed. Perfect for athletes, active individuals, or anyone seeking daily relief, this lotion offers a safe and soothing solution you can trust. Experience the natural power of Tru Releaf’s herbal pain relief lotion and give your body the gentle care it deserves.
ReplyDeleteThanks for posting
ReplyDeletehttps://best DevOps Training institute in Hyderabad
I have been exploring for а little bit foг anу hіgh qualіty articleѕ. Ηaving read this I thought it waѕ гatheг іnfoгmatіve. Ι apрrecіate you taκing the time and effοrt to put this informаtive аrticle togetheг. So Download Free APK and enjoy With Stumble Guys APK Mod.
ReplyDeleteHypic
Inat Pro APK
Bling2APK
Nice blog post...thanks for posting such an amazing content
ReplyDeleteDevops in ameerpet
Nice blog post ...Thanks for sharing
ReplyDeleteDevops course in Ameerpet
Very informative article! The explanation of Windows PowerShell remoting and host-based firewall rules is clear and easy to follow. Thanks for sharing such helpful content!
ReplyDeleteDevops Training Institute in Hyderabad
Thanks for the great explanation of PowerShell Remoting! Your comparison of host-based and user-based remoting gives a solid understanding of when and why to use each method. If you're also preparing for exams, I recommend checking out sat coaching online by Fast Prep Academy to stay focused and organized during your study sessions.
ReplyDelete