Windows PowerShell Remoting: Host Based Investigation and Containment Techniques
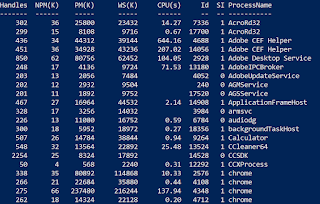
In this blog post I will detail how to perform various incident response techniques using native Windows PowerShell functionality. Each method I explain will be able to be executed remotely to allow for efficient investigation and containment of an individual host . For PowerShell response on mass, I recommend familiarising yourself with the Kansa framework . If you follow my github, you may also notice that many of the techniques listed below are built into my remote powershell triage tool, B2Response , which allows you to perform these actions with ease. Please give it a go and provide feedback! The techniques which I will cover include: 1) Issuing remote command/shell 2) Retrieving/downloading files 3) Checking for running processes 4) Query registry keys 5) PCAP collection 6) Blocking a domain 7) Blocking an IP 8) Quarantining a host Prerequisites All of the techniques listed below utilise PowerShell to remotely manage computers within your IT environment. In order...

